Search This Blog
Microsoft 365 in an Enterprise Environment: Summary & Simple Implementation Guide
Posts
Showing posts from May, 2022
Restrict Access (View only) to org data on Windows 10 Personal device (BYOD)
- Get link
- X
- Other Apps
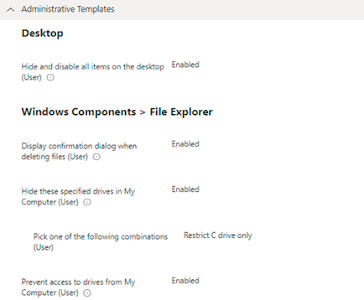
Block users from saving data on System Drive on Intune Managed Device
- Get link
- X
- Other Apps