Recently i delivered a project for Intune Deployment and came up with a requirement as follows
End Users Should not be able to save data locally on C or D Drive, instead they should be allowed to save data only in One Drive for business (synced with System)
Based on the requirement i did my research and found the Following.
- its possible to control the Local System settings on a Azure AD joined Machine and Managed by Intune.
- There is no options to define exceptions in policies to allow data saving in certain folders.
Now most of us will think WIP (windows information protection) policy will help us protecting the data on device, however that's not completely true as .
- User can change the File Ownership to personal if the WIP policy is set to Allow Override.
- User can save the file locally on the system
- User will not be able to copy the data from work file to Personal file if policy is set to Allow override.
- Unenlightened apps cannot differentiate between personal and corporate data as they are not aware of the WIP APIs (not integrated into source code) and if targeted by WIP policy OS will enforce the application to treat all data being used as corporate and apply for the protection on it.
So there is limitation in using WIP to achieve the target.
Now We decided to test Administrative Policies to Block users from Saving Data locally.
Create a Configuration profile
- Login to Endpoint Manager Intune portal https://endpoint.microsoft.com/#home
- Navigate to Devices -> Windows -> Configuration profiles.
- Click on +Create Profile.
- Select Platform: Select Windows 10 and later.
Give the Name & Description and proceed next.
- click on the +Add Settings link to bring up the new blade of the policy configuration wizard. This bring new blade called the Settings Picker with a search box.
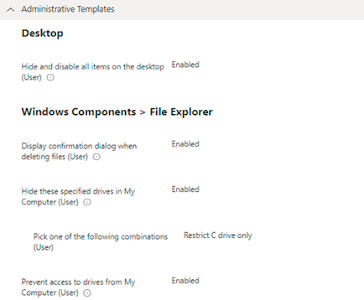
- Expand Settings catalog is – Administrative Templates\Windows Components\File Explorer
- In the “File Explorer” subcategory – Select the settings catalog Prevent access to drives from My Computer
Proceed Next and Configure the policy > enable the Setting and under the Dropdown select the Drive to Block the access
Deploy the policy to the group. User will experience a Pop up stating operation cancelled due to restrictions if they will try to save data on the drive.
You can also hide the Drive from System if you select the settings as per the Image above.
Conclude - Its not Possible to Allow users to save data only on One Drive for Business and restrict on System Drives.
Comments
Post a Comment